Back to articles
Arm Platform Security Architecture: Can It Secure The IoT?

Platform Security Architecture (PSA) is an initiative from Arm that aims to address some of the shortcomings with IoT security. It has the goal to demystify implementation choices and bring coherence to the IoT ecosystem.
Security is one of those eternal topics when IoT discussions take place. It doesn’t look to be fully resolved in the short term, so it’s always good to keep it in mind.
As has been mentioned in previous blogs, many feel that the essentials of security are already with us. The issue is how they are implemented together into a holistic end-to-end solution. It’s akin to having all the ingredients necessary to make a great meal, you just need the right recipe to make everything work together.
Security is essential, and time is of the essence
What's needed is a guarantee of security quality, a unifying benchmark to measure an IoT solution’s security against. Right now, it’s more than a little bit messy.
With such economic promise in IoT, it is no surprise that many established companies have re-aligned their focus towards IoT. But with big rewards, comes big risks. In the scramble to get into pole position, some corners are inevitably getting cut. Well-planned, holistic security seems to be one of them.
Arm Platform Security Architecture
Platform Security Architecture (PSA) is an Arm initiative that aims to address these shortcomings. First, some context. Arm’s 2016 Security Manifesto read:
1. To shift the economics of security:
Security should be affordable throughout the device lifecycle.
2. Making security practical at scale:
IoT cloud operators need the facility to manage vast numbers of devices, securely and efficiently, regardless of the different device types or silicon inside them.
3. Security across the entire value chain:
A key benefit of the IoT lies in the data generated and exchanged, and the analysis and subsequent information extracted from this data. Companies must be able to determine the reliability of the data, to make the shared financial benefits of the ecosystem a reality.
4. Security from the ground up:
A consistent standard of security should be designed into the hardware and firmware of all devices.
5. An industry-wide responsibility:
Security is an industry-wide responsibility. The technology industry, as a whole, needs to step up, collaborate, and adopt a common security best practice in order to address current and future security threats. PSA calls on the ecosystem to take action and raise standards of security, across the board.
How does PSA work?
Arm is well-placed to see much of what needs to happen to make security better, as their processor and other IP are in just about everything that is going into the IoT today. PSA is described by Arm as the framework for securing a trillion devices through a holistic approach to security. It proposes a range of deliverables including threat models, security analyses, hardware, software and API test kits, using industry best practice as its foundation.
Overall it has a goal to de-mystify security implementation choices and bring coherence between all of the different providers in the IoT ecosystem.
PSA is in its early stages and there is likely more to come. But as of today, there are three key phases to applying PSA:
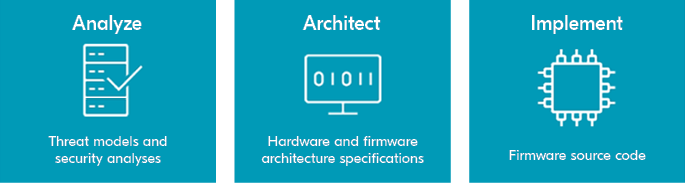
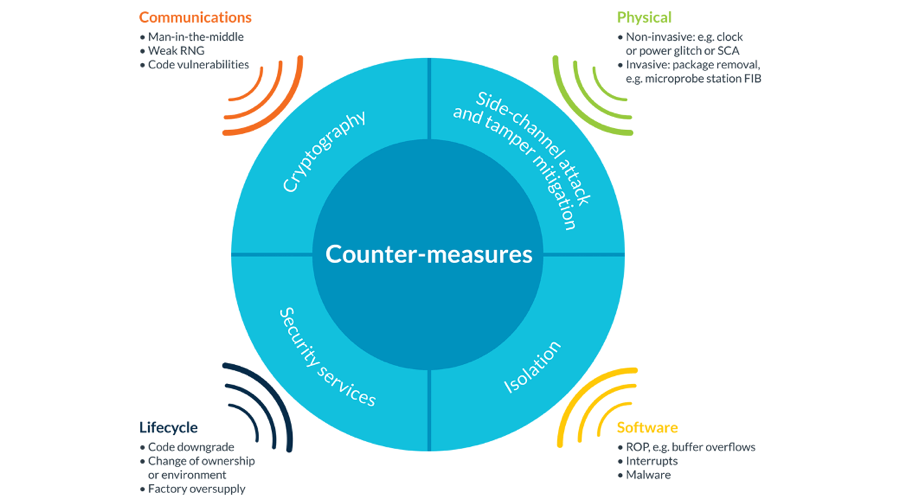
Phase 1. Analysis
This phase looks at the typical use case of an application and where its potential vulnerabilities might be. Different use-cases will yield different security threat profiles. Over time these different profiles should build in number to become a broad set of example cases to base security analysis assessments on. Arm have created 3 example profiles to help demonstrate how this process can work:
• Asset tracker
• Smart water meter
• Network camera
From here a protection profile threat model document can be created. This makes the threat determination and necessary security requirements easy for engineers to follow, even if they do not have a background in security.
Phase 2: Architect
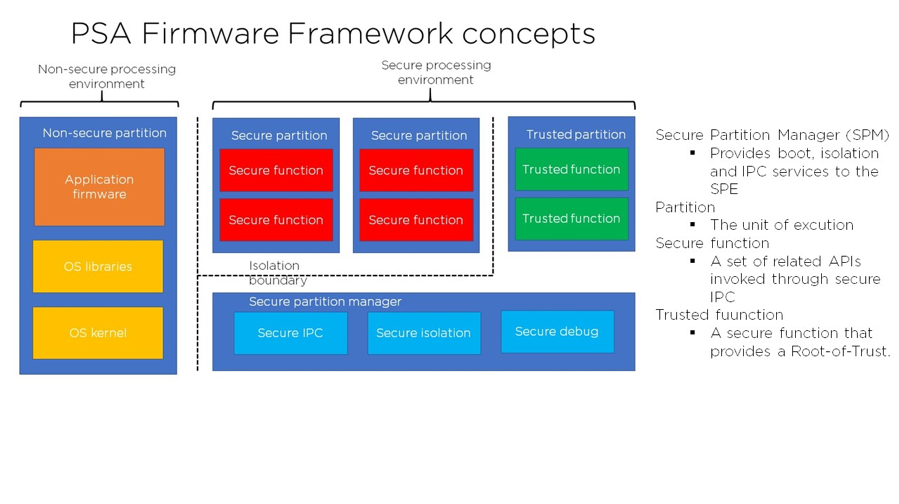
The next phase focuses on creating an architecture that is suitable for delivering the necessary security requirements. PSA specifications consist of a suite of connected documents to help specify this architecture. Elements of this phase include ensuring a fundamental root-of-trust is established for trusted boot and firmware updates.
Click on pic for larger version
Phase 3: Implement
This phase is all about actually building your product with Trusted Firmware-M (TF-M) firmware reference libraries. These reference implementations leverage Arm’s TrustZone technology.
Read more: Arm Trust Zone
As it involves the writing and testing of software, this is likely to be the most complex phase. There will be off-the-shelf firmware libraries for use, but many companies may want to implement their own libraries. This phase is likely to take a little more time to settle down.
Click on pic for larger version
Nordic certification for PSA
The nRF9160, Nordic’s first cellular IoT device supporting LTE-M, NB-IoT and GPS was amongst the very first devices to be certified to PSA level 1. This device features the Arm Cortex-M33 core and TrustZone features associated. TrustZone is a fundamental requirement going forward with the latest Arm processor cores.
Where to next?
Arm’s Platform Security Architecture is at an early stage but holds great potential for unifying the entire IoT value chain into a singular holistic approach to security.
Level 2 certification will be formally introduced later this year. From there more knowledge will come and the best approaches to identify, test for, and minimize security attack vectors and surfaces will be ascertained.
It is a work in progress, but seems to be a well thought-out program of certification. It carries the considerable weight of a company whose technology impacts almost every semiconductor company today.
Nordic are an early PSA partner in the pursuit of an ideal: that all devices are secure, and that users can have legitimate faith in their IoT products.
However far down that road we get, PSA will help improve the patchy security landscape we see today. As Arm say themselves, security should never be optional.
We’ll be covering much more about Arm’s Platform Security Architecture in the coming months, including an in-depth look at the individual phases. In the meantime, you can learn more here.